Bot Attacks Web Apps Or Mobile Apps, posing significant security risks. These automated threats exploit vulnerabilities to compromise app functionality and data.
In the digital era, the prominence of web and mobile applications in business and personal use has skyrocketed, making them prime targets for bot attacks. Cybercriminals deploy bots to perform various malicious activities, ranging from data theft to service disruptions.
As businesses increasingly rely on these platforms to engage with customers, the need for robust security measures becomes paramount. Bot attacks not only jeopardize user privacy but also threaten the integrity and availability of services provided by the apps. Protecting web and mobile applications from such automated threats is a critical aspect of maintaining trust and functionality in the online landscape. Security strategies must evolve continually to outpace the sophisticated techniques used by attackers, ensuring a safe environment for users and service providers alike.
The Rising Threat Of Bot Attacks
The Rising Threat of Bot Attacks is more severe than ever. Bots, automated software programs, are increasingly targeting web and mobile apps. They perform tasks that mimic human interactions. Bot Attacks Web Apps Or Mobile Apps, These attacks can disrupt user experience and cause significant damage to business operations.
Types Of Bots Targeting Apps
- Scraping Bots: They steal content and data from websites.
- Spam Bots: These bots flood apps with irrelevant messages.
- Login Bots: They attempt to access accounts by guessing passwords.
- DDoS Bots: They overload servers, making the apps unavailable.
Consequences Of Unchecked Bot Activity
Uncontrolled bot traffic can have serious consequences:
| Impact | Details |
|---|---|
| Security Risks | Increases the risk of data breaches and theft. |
| Performance Issues | Slows down app performance, affecting user satisfaction. |
| Increased Costs | Increased server load leads to higher operational costs. |
| SEO Impact | Negative effects on SEO if bots create spam content. |
Identifying Bot Attacks
Bot Attacks Web Apps Or Mobile Apps. Bots can disrupt operations, steal data, and damage your reputation. Knowing the signs of a bot assault is key to protecting your digital assets. Let’s explore how to identify when bots are attacking your app.
Signs Your App Is Under Bot Assault
Bots often leave distinct patterns in their wake. Look for these red flags:
- Spike in traffic: An unexpected surge could mean bots are at work.
- Unusual patterns: Repeated actions at superhuman speed suggest bot activity.
- High bounce rates: Bots visit but don’t engage, leading to high bounce rates.
- New account creation: Mass sign-ups may indicate a bot-driven fake account creation.
- Failed login attempts: Repeated failures can be bots trying to gain access.
Tools For Detecting Malicious Bots
Equip your app with the right tools to spot and stop bots:
| Tool | Function |
|---|---|
| Web Application Firewalls (WAFs) | Block malicious traffic before it reaches your app. |
| CAPTCHAs | Challenge tests that distinguish humans from bots. |
| Bot Management Solutions | Analyze traffic patterns to identify and manage bots. |
| Analytics Tools | Monitor and alert on unusual traffic spikes and patterns. |
Regularly review and update your detection strategies to stay ahead of evolving bot tactics.
Bot Attack Vectors
Web and mobile applications face constant threats from automated bots. These bots can disrupt services, scrape data, and exploit weaknesses. Understanding Bot Attack Vectors is crucial to safeguarding apps effectively.
Common Entry Points For Bots
Bots often look for the easiest way into an app. Here are some typical entry points:
- Public APIs: Bots use these as gateways for data theft.
- User Login: They attempt to break passwords and gain access.
- Payment Gateways: Bots target these for credit card fraud.
How Bots Exploit App Vulnerabilities
Bots can be very sneaky and use different ways to harm apps:
| Vulnerability | Bot Exploit Method |
|---|---|
| Weak Authentication | Credential stuffing to access user accounts. |
| Rate Limiting | Slow bots evade detection and slowly harm systems. |
| Input Validation | Bots inject malicious code into corrupt databases. |
Protecting apps requires a strong defense against these bot attacks. Be careful and keep your security systems up to date.
Human Vs. Bot: Knowing The Difference
In the digital age, distinguishing between human users and bots has become crucial for web and mobile app security. Bots can mimic human behavior, making it challenging to differentiate them from real users. Understanding the nuances between bot and human interactions helps in enhancing security measures.
Bot attacks web apps or mobile apps android
Bot attacks on web apps or mobile apps, including Android applications, are increasingly common and pose significant security threats. These attacks involve automated programs, or bots, that attempt to exploit vulnerabilities in the applications.
Bots can perform various malicious activities such as credential stuffing, scraping data, launching distributed denial-of-service (DDoS) attacks, and conducting fraud. These automated threats can compromise sensitive user information, degrade app performance, and lead to substantial financial and reputational damage for businesses.
Implementing robust security measures, such as rate limiting, CAPTCHA challenges, and advanced bot detection algorithms, is essential to protect web and mobile apps from these pervasive threats.
Behavioral Analysis To Distinguish Bots
Behavioral analysis is a powerful tool in detecting bots. It looks at patterns in user activity. Bots often exhibit repetitive, predictable actions, whereas humans show more complexity and randomness in their behavior.
- Bots may complete tasks faster than humanly possible.
- Humans typically have varied mouse movements and keystroke patterns.
- Session durations and page navigation paths can also indicate bot activity.
By analyzing these and other behavioral signals, systems can flag potential bots for further review or restriction.
Implementing Captcha And Other Challenges
CAPTCHA is a common method to separate humans from bots.
| Type | How It Works | Example |
|---|---|---|
| Text-based | Users type letters or numbers from a garbled. | Identifying skewed text. |
| Image-based | Users select images matching a specific theme. | Picking out all the traffic lights. |
| Interaction-based | Users perform a simple task to prove they’re not bots. | Dragging a slider to complete a puzzle. |
Aside from CAPTCHA, biometric challenges and two-factor authentication add extra layers of protection. These methods ensure that bots cannot easily mimic human responses.

Layered Defense Strategies
Layered Defense Strategies are crucial in protecting web and mobile apps from bot attacks. Imagine your app as a fortress. Just like a castle needs strong walls, a moat, and guards, your app needs multiple layers of defense. These strategies work together to keep bots out, just like keeping the enemy away from the castle.
The Role Of Firewalls And Proxies
Firewalls and proxies act as the first line of defense for your app. They are like the tall, strong walls around a castle. Firewalls check incoming traffic and block harmful bots. Proxies hide your app’s location, making it harder for bots to attack.
- Firewalls filter traffic based on set rules.
- Proxies serve as intermediaries to protect your app’s real IP address.
Using Rate Limiting To Thwart Bots
Rate limiting is like the guards at the castle gates. It controls how often someone can try to enter. If a bot tries to access your app too many times too quickly, rate limiting will block it. This keeps your app safe from too many fake visits.
| Rate Limiting Benefits |
|---|
| Prevents spam and abuse |
| Protects against brute-force attacks |
| Helps the app run smoothly for real users |
Advanced Bot Detection Techniques
As web and mobile apps face ever-evolving threats, the need for advanced bot detection techniques has never been greater. Sophisticated bots mimic human behavior, making them challenging to identify. Yet, innovative strategies are rising to keep these unwanted visitors at bay.
Machine Learning In Bot Identification
Machine learning stands at the forefront of bot detection. This technology adapts and learns from patterns, distinguishing between human users and bots. It analyzes vast amounts of data to recognize subtle anomalies.
- Behavior Analysis: Machine learning observes how users interact with apps.
- Anomaly Detection: It spots unusual behavior that could indicate a bot.
- Continuous Learning: The system evolves, catching new bot tactics over time.
Real-time Analytics For Bot Mitigation
Real-time analytics play a key role in bot mitigation. This technique processes data instantly to block bots before they cause harm.
| Feature | Benefit |
|---|---|
| Instant Detection | Identifies bots in milliseconds. |
| Dynamic Response | Adjusts defenses based on threat level. |
| User Experience | Keeps apps fast and responsive for real users. |
Mobile App-specific Concerns, Bot Attacks Web Apps Or Mobile Apps
Mobile apps face unique challenges when it comes to security. Attackers often target these applications with sophisticated bots. These bots can mimic human behavior. They can steal data or disrupt services. Protecting mobile apps requires specific strategies. Developers must secure both the app and its backend APIs.
Securing Apis Against Bots
APIs are gateways for mobile apps to access data. They need protection from bot attacks. Here are some steps to secure APIs:
- Implement Rate Limiting: This prevents bots from making too many requests in a short time.
- Use API Keys: They ensure that only authorized apps can access your API.
- Deploy CAPTCHA: It challenges bots with tasks that are easy for humans but hard for bots.
These steps help keep your API safe from unauthorized access and abuse.
Mobile SDKs For Enhanced Security
Mobile SDKs are tools that help developers build secure apps. They come with built-in security features. Here’s how SDKs enhance app security:
| Feature | Description |
|---|---|
| Fraud Detection | Identifies unusual patterns that could indicate bot activity. |
| Data Encryption | It keeps data safe even if intercepted by bots. |
| Biometric Authentication | Ensures only real users can access the app. |
By integrating these SDKs, developers can build more secure mobile apps. They prevent bots from causing harm.
User Authentication And Access Management
User Authentication and Access Management are critical in protecting web and mobile apps from bot attacks. Bots can mimic human behavior, making them a real threat. They try to access user accounts, steal data, and disrupt services. Strong user authentication stops bots from entering systems. It checks if a user is who they claim to be. Access management controls what a user can do after logging in. Together, they guard against unauthorized access and bot activity.
Multi-factor Authentication (MFA) To Combat Bots
Multi-factor authentication (MFA) adds extra security layers. Users must provide several proofs of identity. This often includes something they know, something they have, and something they are. Bots find it hard to bypass MFA, as they can’t easily fake these proofs.
- Passwords: Something users know.
- Security tokens: Something users have.
- Biometrics: Something users are.
By using MFA, apps reduce the risk of bot attacks. Users feel safe knowing multiple checks protect their accounts.
Role-based Access Controls (RBAC)
Role-Based Access Controls (RBAC) define what each user can do within an app. Users get access only to what they need for their role. This limits what bots can do if they get in.
| Role | Access Level |
|---|---|
| Admin | Full access to all features |
| User | Limited access to necessary features only |
| Guest | Very limited access, mostly read-only |
RBAC helps ensure that even if bots breach the first line of defense, their impact remains minimal. Apps stay safer and more secure.
Content Delivery Networks (CDN) And Bot Management
Content Delivery Networks (CDNs) and Bot Management play a crucial role in safeguarding web and mobile applications. CDNs not only ensure fast content delivery but also provide a layer of defense against malicious bot traffic. Effective bot management through CDNs can protect applications from various threats. Let’s explore how CDNs contribute to both prevention and the security features you can enable for robust bot management.
How Cdns Can Help Prevent Bot Traffic
CDNs are designed to distribute content across multiple servers globally. This setup provides a unique advantage in bot traffic prevention:
- Geographical Distribution: By serving content from the nearest server to the user, bots are more easily identified and managed.
- Load Balancing: Spreading requests across servers prevents bot-induced traffic spikes from overwhelming resources.
- IP Blacklisting: CDNs can block traffic from known malicious IPs, stopping bots before they reach your app.
- Rate Limiting: This feature limits the number of requests a user can make within a certain timeframe, curbing bot activity.
Cdn Security Features To Enable
Activating specific features within your CDN can enhance your app’s security against bots. Consider enabling the following:
| Feature | Description | Benefit |
|---|---|---|
| Web Application Firewall (WAF) | Filters and monitors HTTP traffic between a web app and the Internet. | Prevents common web threats and automated attacks. |
| Bot Scoring | Assesses each visitor’s likelihood of being a bot based on behavior. | Allows legitimate users while blocking or challenging suspicious ones. |
| SSL/TLS Encryption | Secures data transfer, ensuring data integrity and confidentiality. | Thwarts man-in-the-middle attacks and eavesdropping attempts. |
| Custom Rules | Allows the creation of tailored rules to address unique threats. | Enhances security posture by adapting to new bot patterns. |
Secure Coding Practices
Secure Coding Practices are essential in protecting web and mobile apps from bot attacks. These practices help developers write code that is tough for bots to exploit. Let’s explore some key strategies to enhance your app’s security against these automated threats.
Bot detection tools
Bot detection tools are essential in safeguarding web and mobile applications from malicious automated activities. These tools use advanced algorithms and machine learning techniques to differentiate between genuine users and bots by analyzing patterns in behavior, network traffic, and interaction anomalies.
Features such as rate limiting, IP reputation analysis and device fingerprinting enhance their efficacy. By employing CAPTCHA challenges and behavioral biometrics, bot detection tools effectively block unwanted traffic while ensuring a seamless experience for legitimate users. T
hese tools are crucial for preventing security breaches, data theft, and fraudulent activities, thus maintaining the integrity and performance of digital platforms.
Writing Bot-resistant Code
Developing bot-resistant code is a proactive approach to secure your apps. Focus on these points:
- Validate inputs rigorously: Ensure all data entering your system is checked.
- Use CAPTCHAs: These challenges distinguish humans from bots.
- Limit login attempts: This prevents bots from trying passwords repeatedly.
These steps make your app tough for bots to crack.
Regular Code Audits And Reviews
Regularly checking your code can catch and fix security gaps. Here’s how:
- Plan audits frequently: Schedule them to ensure consistent security.
- Use automated tools: They help identify vulnerabilities fast.
- Peer reviews: Have other developers check your code.
This process keeps your app’s defenses up to date.
| Task | Tools | Frequency |
|---|---|---|
| Input Validation | Security Libraries | Daily |
| CAPTCHA Implementation | Google reCAPTCHA | As needed |
| Login Limits | Custom Scripts | Update regularly |
Follow these tables for best practices.
Educating Users And Staff
The section ‘Educating Users and Staff’ is key in fighting bot attacks on web and mobile apps. It ensures everyone knows how to spot and stop these threats.
Training On Security Best Practices
Regular training sessions are crucial. They keep security skills sharp and up to date. Here’s what to include:
- Password management – Creating strong, unique passwords.
- Recognizing phishing attempts – Identifying suspicious emails and links.
- Using secure networks – Avoiding public Wi-Fi for sensitive tasks.
Interactive quizzes can help reinforce these practices. They make learning fun and engaging.
Creating Awareness About Bot Threats
Raising awareness about bot threats is vital. It helps staff and users stay alert. Key points include:
| Type of Bot Attack | Signs to Watch For | Preventive Measures |
|---|---|---|
| Credential Stuffing | Multiple failed login attempts | Implement multi-factor authentication |
| DDoS Attacks | Slow network performance | Upgrade network security settings |
| Scraping | Unusual traffic spikes | Monitor and analyze web traffic |
Informative posters and regular security updates can help keep everyone informed and prepared.
Incident Response Planning
Incident Response Planning is a critical step for businesses to ensure they can quickly and effectively deal with bot attacks on their web or mobile apps. A well-crafted response plan minimizes damage and restores operations promptly.
Preparing For A Bot Attack
Being prepared is the first line of defense. Here’s how:
- Identify critical assets. Know what needs the most protection.
- Train your team. Make sure they recognize and respond to threats.
- Create clear procedures. Outline steps for different attack scenarios.
- Implement detection tools. Use software to spot unusual activities.
- Regularly update defenses. Keep security measures current.
Post-attack Analysis And Recovery
After an attack, it’s important to bounce back. Focus on these areas:
- Analyze the breach. Look into how the bot penetrated your defenses.
- Assess the impact. Determine what was affected and to what extent.
- Communicate with stakeholders. Keep everyone informed about the issue.
- Repair the damage. Fix vulnerabilities to prevent future attacks.
- Review response efficiency. Improve plans for next time.
| Step | Action |
|---|---|
| 1 | Isolate affected systems |
| 2 | Update security protocols |
| 3 | Restore from backups |
| 4 | Monitor for anomalies |
Legal And Compliance Aspects
Bot attacks on web and mobile apps raise serious legal and compliance issues. Companies must navigate complex laws to protect user data and their operations. A clear understanding of the legal framework is essential for any business operating online.
Understanding The Legal Framework
Bots can disrupt the normal functioning of apps. This disruption may breach laws. Different countries have different rules against unauthorized system access. Businesses need to know these laws to protect themselves. They must make sure their security practices are legally sound.
Ensuring Compliance With Data Protection Laws
Data protection laws like GDPR in Europe and CCPA in California are strict. They require businesses to safeguard personal data. Failing to prevent bot attacks can lead to data breaches. This puts companies at risk of heavy fines. Regular security audits and updates are key. Businesses must stay compliant to avoid legal penalties.
- Know the laws in your region and internationally.
- Update security measures regularly to keep pace with evolving threats.
- Conduct audits to ensure ongoing compliance.
- Train your staff on best practices for data protection…
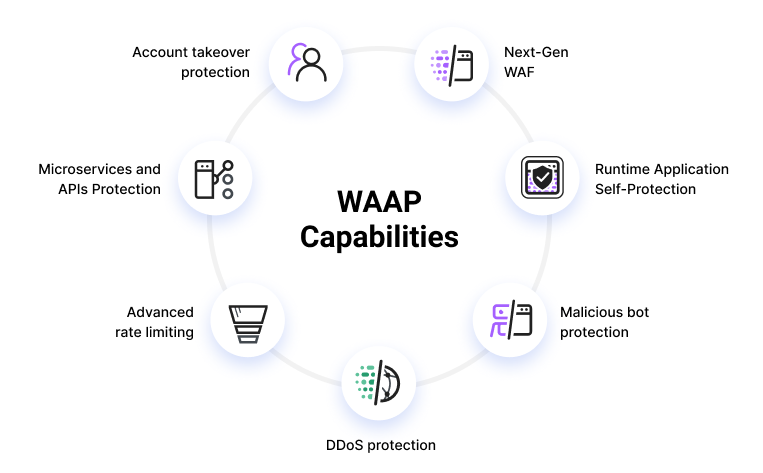
Credit: www.imperva.com
Future Of Bot Mitigation
As web and mobile apps evolve, so do the threats against them. Bot attacks are a growing concern. The future of bot mitigation is a hot topic for businesses and cybersecurity experts. It’s all about staying one step ahead. Let’s dive into the emerging technologies and strategies that will help protect your digital assets.
Emerging Technologies In Bot Defense
New technologies are shaping the battle against bots. Artificial Intelligence and Machine Learning lead the charge. They help systems learn from attacks and adapt quickly. Behavioral biometrics analyze user interactions. They spot bots by looking at how users touch, swipe, or type.
- AI and ML: Systems detect and respond to threats faster.
- Behavioral Biometrics: Differentiate between humans and bots by user behavior.
- Next-Gen CAPTCHAs: More complex puzzles that are harder for bots to solve.
Staying Ahead Of Sophisticated Botnets
Botnets are becoming smarter. But so are the ways to fight them. Real-time defense is crucial. It means stopping bots the moment they attack. Threat intelligence networks gather data from across the globe. They help predict and prevent attacks.
| Strategy | Description |
|---|---|
| Real-Time Defense | Instantly reacts to and blocks bot attacks. |
| Threat Intelligence Networks | Shares data globally to stop bots before they strike. |
| Collaborative Efforts | Companies and cyber experts work together against bots. |
By using these strategies, businesses can stay ahead of botnets. They can keep their web and mobile apps safe. The future of bot mitigation is smart, fast, and collaborative.
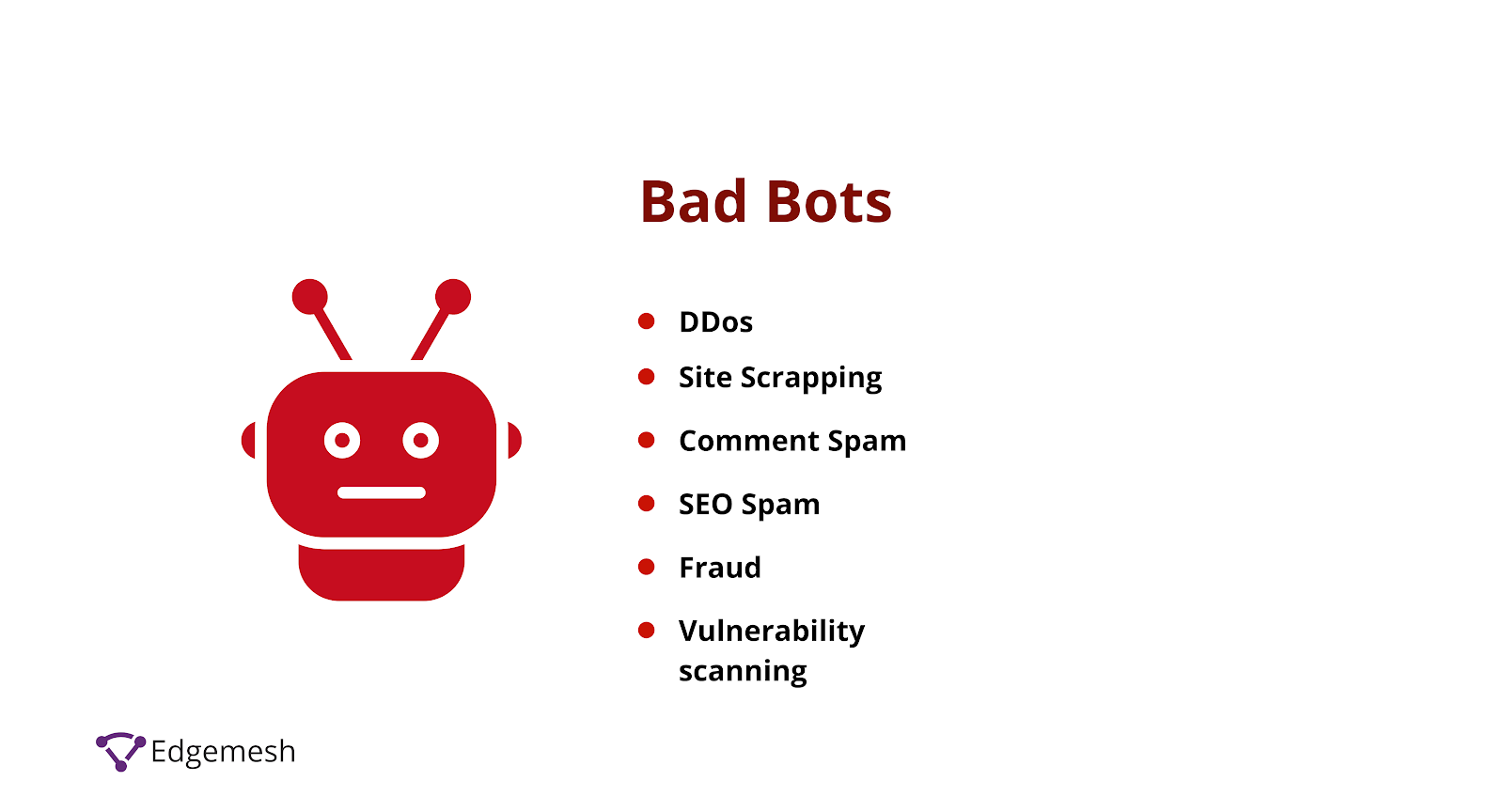
Credit: edgemesh.com
Frequently Asked Questions
How To Tell If A Bot Is Crawling Your Site?
Check your website’s server logs for unusual spikes in traffic, particularly from a single IP address. Use tools like Google Analytics to identify patterns indicative of bot behavior, such as rapid page crawling.
How Do You Know If Bots Are Visiting Your Website?
Check your website analytics for patterns like high bounce rates, fast session durations, or unusual traffic spikes, which can indicate bot visits.
What Is Bot In Mobile?
A bot in mobile refers to a software application designed to automate tasks on smartphones, such as messaging or scheduling.
How Do You Detect Bot Activity?
Detect bot activity by monitoring unusual traffic patterns, high-speed actions, repetitive tasks, and anonymous IP addresses. Use CAPTCHA tests and analyze user behavior for inconsistencies.
Conclusion
Understanding the threats posed by bot attacks is critical for the security of both web and mobile applications. By implementing robust defensive strategies and staying informed about the latest trends, developers and businesses can safeguard their digital assets. Vigilance and proactive measures are your best allies in the evolving landscape of online security.
Protect your apps, protect your users.

I Am a tech specialist writer and blogger based in the USA, UK, Canada and Australia. I have been working with technology three long years. And I give trips on various problems , Idea and solution. I have a lot of experience with technology And I share them here.

